Introduction #
MSPMagic uses various methods to authenticate to your customers Microsoft 365 tenants.
We always prefer to use Modern Authentication following the Microsoft Secure Application Model, however this is not always supported by Microsoft for all services.
Microsoft Teams supports Modern Authentication for some settings, while others still rely on the older Skype for Business service and often requires the use of Basic Authentication.
In order for MSPMagic to use Basic Authentication, the tenant needs to be configured correctly to allow this authentication method where it is used, while blocking unwanted access using Basic Authentication.
Authentication Methods used by each service
| Service | Authentication Method |
| Partner Center | Modern – Secure App Model via Direct Access |
| Azure AD | Modern – Secure App Model via Delegate Admin |
| Exchange Online | Modern – Secure App Model via Direct Access |
| SharePoint Online | Modern – Secure App Model via Direct Access |
| Microsoft Teams | Basic – Global Administrator via Direct Access, and; Modern – Secure App Model via Delegate Admin |
| Endpoint Manager | Modern – Secure App Model via Delegate Admin |
Security Defaults #
SharePoint Online settings will not be available if your customers tenant has Security Defaults enabled.
Security Defaults automatically blocks all legacy authentication methods.
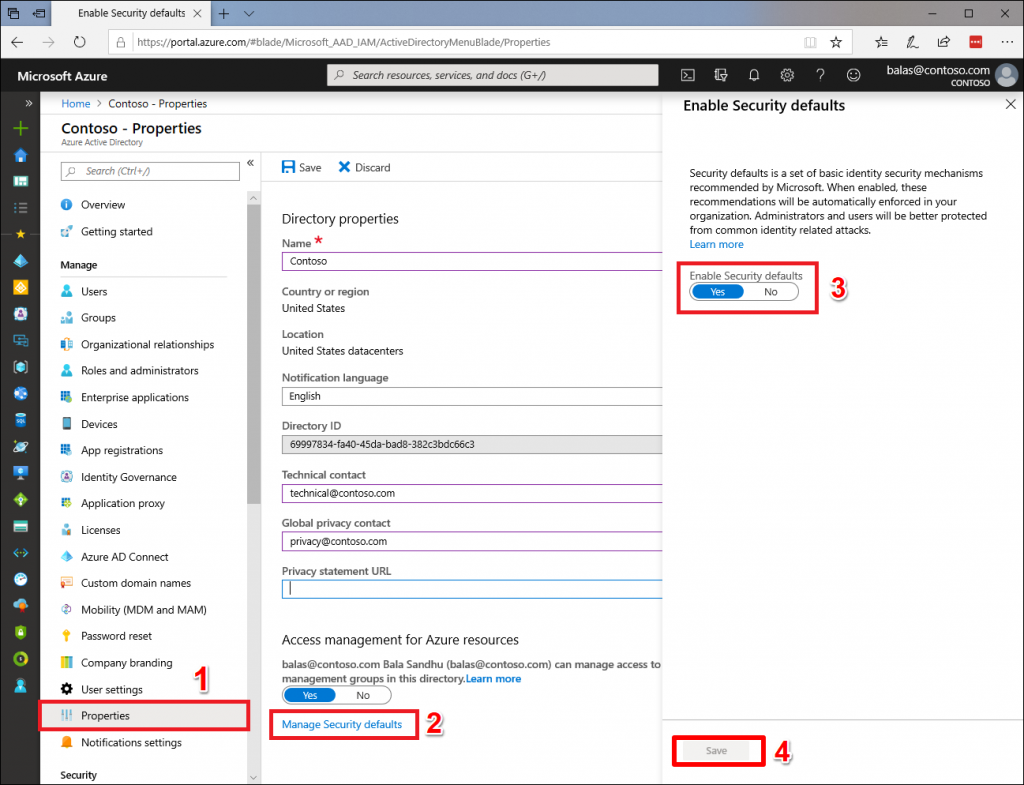
To Disable Security Defaults
- Sign into your customers Azure Active Directory (https://aad.portal.azure.com) as the Global Administrator
- Navigate to Properties -> Manage Security defaults and then Select No under Enable Security defaults
- Click Save to apply the setting.
When disabling Security Defaults, MSPMagic recommends you replace the settings with Conditional Access policies to ensure that access to your customers tenant is secured. Please see the following guide: Replacing Azure AD Security Defaults with Conditional Access Policies
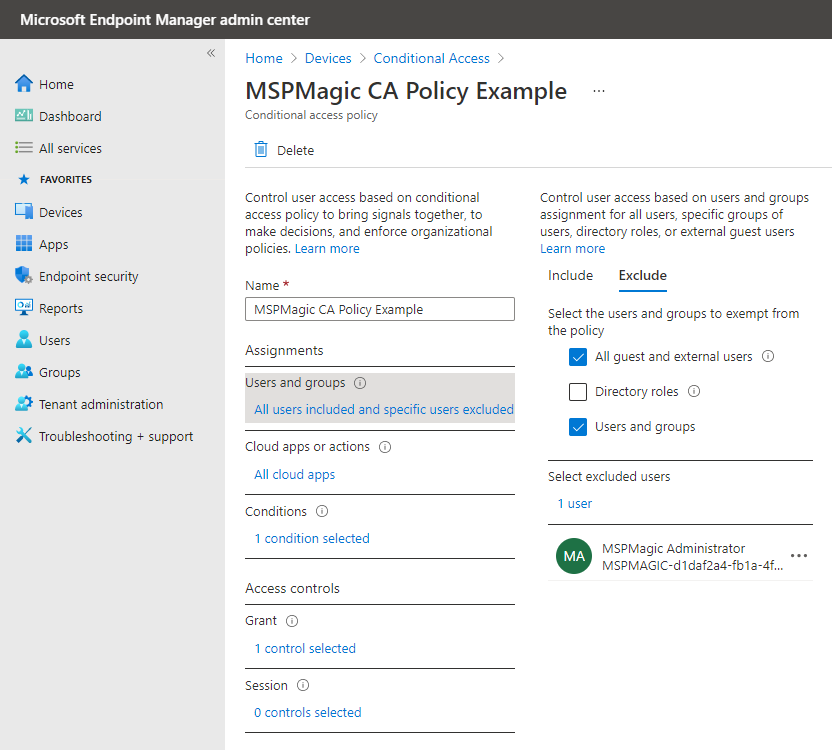
Conditional Access Policies #
If there are any Conditional Access Policies assigned in the customer tenant, the MSPMagic Administrator Global Admin account must be excluded from the policies and our IP address is to be whitelisted.
The use of Conditional Access Policies requires that the tenant has at least a single license of Azure AD P1 or P2.
IP Address: 20.188.223.13/32
Display Name: MSPMagic Administrator
User Principal Name: MSPMAGIC-<PartnerTenantGUID>@<TenantDefaultDomainPrefix>.onmicrosoft.com
Please see the following procedure:
- Sign into your customers Endpoint Manager Portal (https://endpoint.microsoft.com) as the Global Admin
- Navigate to Devices -> Conditional Access
- For each Conditional Access Policy, add the MSPMagic Administrator to the Excluded.