Introduction #
This setting allows you to automatically block sign in to Azure AD accounts which have been inactive for a nominated period of time (eg 30 days).
In general, blocking or disabling inactive accounts can be an effective security measure because it can help prevent unauthorized access to sensitive information and reduce the risk of data breaches.
Several security frameworks recommend blocking or disabling accounts that have been inactive for a certain period of time as a security measure.
For example, the Center for Internet Security (CIS) Controls recommend disabling inactive accounts after a certain period of time as a security measure. The specific time period may vary depending on the organization’s policies and the sensitivity of the information being protected.
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) also recommends disabling or deactivating inactive accounts as a security measure. According to NIST, “Disabling inactive accounts reduces the attack surface, as it limits the potential for unauthorized access to the system and its resources.”
Other security frameworks, such as the ISO/IEC 27001 standard, the Payment Card Industry Data Security Standard (PCI DSS), and the Essential Eight in Australia, also recommend disabling or deactivating inactive accounts as a security measure.
License Requirement #
Azure Active Directory Premium 1 or Azure Active Directory Premium 2
User Impact #
High
When set to enforce, sign in to Azure AD accounts which have been inactive for longer than the specified period will be blocked. Use with caution.
We also recommend excluding any break-glass accounts, such as global administrators, to ensure that MSPMagic does not attempt to block their sign-in.
Parameters #
Days of inactivity – The number of days after which an account should be blocked. (Min – 7, Max – 365)
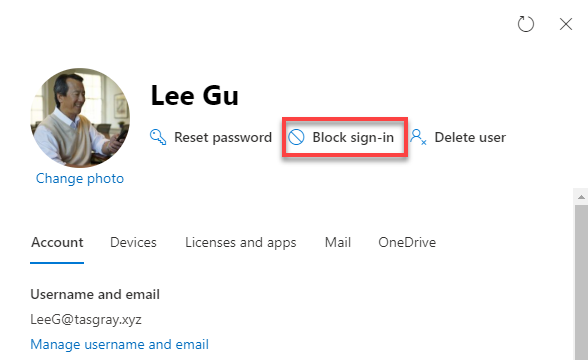
Admin Portal Reference #
Sign in status can be managed from the Microsoft 365 Admin Portal and the Azure Portal.
PowerShell Reference #
Update-MgUser -UserId <userprincipalname> -AccountEnabled:$falseAdditional Notes #
How inactivity period is calculated #
MSPMagic takes three factors in to consideration when calculating the number of days since an account last signed in.
LastSignInDateTime and LastNonInteractiveSignInDateTime – Accounts which have signed in at least once #
MSPMagic will refer to the LastSignInDateTime and LastNonInteractiveSignInDateTime properties of a user object in Azure Active Directory to determine the last time a sign in occured for the account. When both fields have a value, the most recent value will be used as the last sign in date. If neither of these dates are within the inactivity threshold the account will be flagged as inactive and MSPMagic will attempt to block the sign in.
Difference between Interactive and Non-interactive sign ins #
Interactive user sign-ins: Sign-ins where a user provides an authentication factor, such as a password, a response through an MFA app, a biometric factor, or a QR code.
Non-interactive user sign-ins: Sign-ins performed by a client on behalf of a user. These sign-ins don’t require any interaction or authentication factor from the user. For example, authentication and authorization using refresh and access tokens that don’t require a user to enter credentials.
DateCreated – Accounts which have never signed #
When an account has never signed in, MSPMagic calculates the number of days since the last sign-in for an account by using the date of account creation. For instance, consider a user account that was created on November 1, 2022. If the current date is December 1, 2022 and the inactivity threshold is 30 days, MSPMagic would determine that this account has been inactive for 31 days, since the user has not signed in during that time and would attempt to block the sign in.
Accounts with administrative roles #
Accounts which are assigned an adminstrative role in Azure Active Directory cannot be blocked by our automation. Attempting to block these accounts will result in an error, which is displayed in the compliance message. Since we are unable to block the account, the target will be marked as non-complaint and require manual blocking by an administrator before being reported as compliant.
Accounts synchronised from on-premises Active Directory #
MSPMagic will only block sign in to accounts which are ‘cloud only’. Accounts which are synchronised from an on-premises Active Directory cannot be blocked, as the next sync will overwrite the change. For this reason, accounts which are synchronised from an on-premises directory will be flagged as non-compliant and require you to block them from the Active Directory before being reported as compliant.
Guest Users #
Guest users are ignored by this setting and marked as compliant.
If Action is set to Notify #
If an account has not signed in or was created for at least as many days as specified in the Days of Inactivity parameter it will be marked as non-compliant.
If an account has signed in or was created less than the number of days specified in the Days of Inactivity parameter it will be marked as compliant.
If Action is set to Enforce #
If an account has not signed in or was created for at least as many days as specified in the Days of Inactivity parameter the sign in will be blocked and marked as compliant-fixed. There are some exceptions to this, as specified in Additional Notes.
If an account has signed in or was created less than the number of days specified in the Days of Inactivity parameter it will be marked as compliant.
If license requirement is not met #
The setting will report as non-compliant if the tenant does not meet the license requirement.



